|
|
||||
|
|
||||
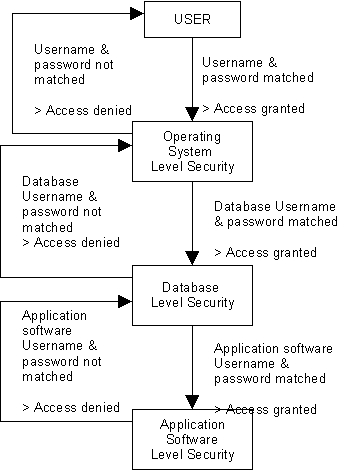
To ensure quality data, data security is required. Data security could be maintained in several ways
such as at the operating system level, the database level and the developed system level. If the
system runs under a client server architecture in a network environment (LAN/WAN), the user must
have the right to access the network which is under a workgroup, after that if s/he wants to access
to the database system a database level authentication password need to be provided. Moreover
access rights to entry screens for data manipulation must be maintained for the user level. As an
example the data entry technician can only input the data into the system, but they never have
access to modify the data. Another level user, i.e. supervisor level user can modify it.
 During a database system design the system/software designer should design the system in such
a way that different levels of user can access/manipulate the data file according to his/her
permission.. As an example the Master data file (Ex. Individual info) must be restricted from the
common user, only the administrative/super level user can access to that.
Moreover there are several ways for protecting systems and data:
Data backup: Data backup is essential, whether data is copied to other hard drives, tapes, optical
disks, or even systems in other locations.
Theft protection: Theft of equipment can cause serious downtime, even if data has been backed
up, considering replacement and reconfiguration costs. You can bolt equipment to desktops and
floors, lock equipment in special rooms, and hire staff to look over equipment 24 hours a day.
Protecting against fire and natural disasters: Consider installing special fire-prevention
equipment, such as halon gas systems, to reduce fire loss. To protect against natural disasters,
consider what is necessary to protect the physical infrastructure. Alternative data centers may be
necessary. Gasoline-powered generators can supply power to servers and workstations when
electricity is cut off.
Recovery: In the event of a physical security breach, hacker attack, fire, earthquake, or other
disaster, you need to get systems back online as soon as possible.
Management style: There are advantages to both centralized management and distributed
management. To centralize management, move network resources- servers, hubs, switches,
routers, and other equipment-to central locations where trained staff can manage the systems in
secure and protected areas. However, doing so puts you at greater risk of catastrophes such as
earthquakes and fires. An alternative is to distribute network resources and automatically replicate
data to remote sites on a regular basis. Use high-speed data links between the sites.
Fault tolerance: Network components should be protected against failure with techniques such as
disk mirroring, disk duplexing, server duplexing, clustering, load balancing, replication, inverter
power systems and a variety of other techniques, including the construction of multiple data centers
Diskless devices: Diskless workstations don't have disk drives, so users can't download valuable
data or upload information in an unsupervised environment
Security: Intruders may physically attack your system or gain access across unsecured
networks.
Administration: Network administrators need to know all the ins and outs of network operating
systems and their security features to protect against attacks, mismanagement, and data
corruption or loss.
Training: Properly trained users are your best resource against security breaches, attacks,
mistakes, lost data, and so on.
Tracking and auditing: Be sure logs and tracking utilities are enabled so you can track down
problems after they occur. |
||||